When an organization has made the decision to implement a PAM tool, it is important to source the right supplier. There is a variety of capabilities that are grouped under the heading ‘PAM’. It depends on the risks to be covered to determine which capabilities contribute the most to your organization. Often times it is sufficient to implement a limited number of capabilities to reduce the risk to an acceptable level.
Risk areas and elements
In the table below, the risks are linked to the NIST elements, which PAM element supports the indicated reason. +’s indicate the extent to which an element contributes to reducing the risks in the indicated areas. This is a starting point which should be further developed based on your own analysis, as described in the document PAM Checklist.
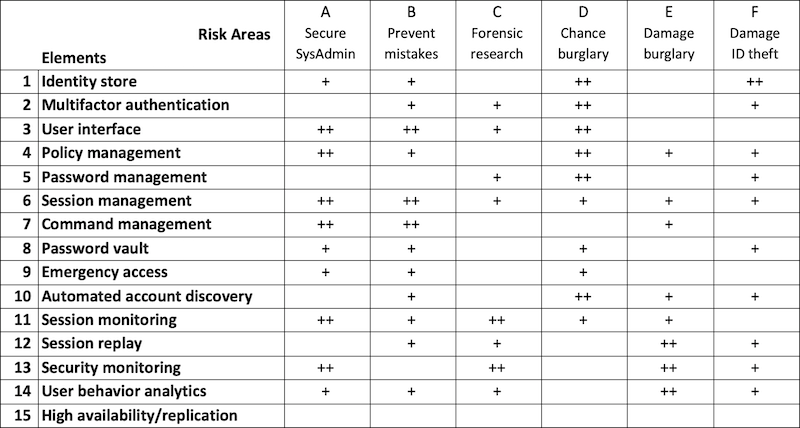
Risk areas for PAM
- Secure management of system administration - Being able to tailor the rights of external and internal administrators to tasks to be performed by them and to view their activities to ensure or improve the quality of their work.
- Preventing errors and mistakes - Preventing administrators from accidentally causing incidents with high privileges.
- Forensic investigation after calamities - Being able to analyze a calamity, trace the cause and analyze the solution actions.
- Reduce the risk of digital burglary - Preventing an ID theft or burglary attempt from succeeding.
- Limiting damage after digital burglary - Limiting the potential damage resulting from a successful digital intrusion.
- Limiting damage after identity theft - Preventing after ID theft of an administrator account from causing (too much) damage to the thief.
NIST Elements
The elements are based on the classification as established by NIST:
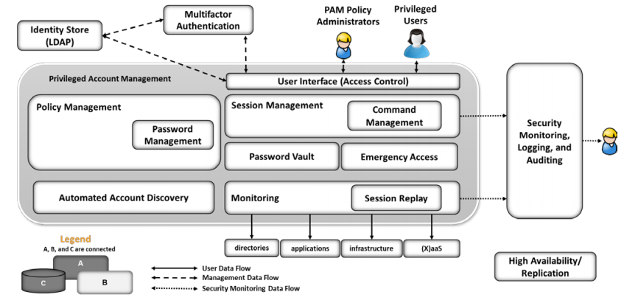
The solid lines represent the flow of user data between privileged users and systems. The dashed line are the management data flow between PAM architecture components. The dashed lines represent the data flow (logs) of the security monitor.
- The Identity Store provides identity records specific to the organization’s privileged users.
- Multifactor Authentication enables a higher level of authentication for privileged users.
- The User Interface provides login authentication and a user-to-PAM system interactive interface that users work with to set up or request work sessions for each system they manage or access to perform their work functions.
- Policy Management monitors enterprise access and control policies for privileged users, such as for instance limiting sessions for privileged users to four hours.
- Password Management monitors the company’s password policy.
- Session Management enforces access and control policies within each work session, such as restricting sessions to SSH or RDP or limiting the allowed use of applications on the target system.
- Command Management limits the commands a person can use.
- Password Vault provides secure storage of current passwords for each privileged account.
- Emergency Access provides access in unpredictable or emergency situations for unexpected users (privileged or non-privileged).
- Automated Account Discovery searches the infrastructure for the existence of privileged accounts, such as domain administrators or accounts that have a high level of authorization directly or indirectly (by assumption of privileges).
- Session monitoring (Monitoring) provides a mechanism to identify, record, and alert on anomalous activity, as well as for real-time training for use of privileged accounts.
- Session Replay provides the ability to revisit sessions. This can be done for training purposes, or for forensics.
- Security Monitoring, Logging, and Auditing provides logging, analysis, and alerting components, generally called security information and event management (SIEM).
- Usage Behavior Analytics (UBA) monitors the activity of privileged users for activities or actions that are considered unexpected or outside a recognized pattern of activity.
- High Availability and Replication ensures the availability of the PAM solution.
©Steven van der Linden, June 2021


